Blog
On the Verge of Polymorphic Mobile Malware?
By TrustGo Security Labs On February 22, 2012 In Security
Yesterday (2/21/2012), TrustGo Security Labs uncovered a significant evolution of the notorious GinMaster malware. Our tests indicate the new variant of GinMaster can successfully evade detection by all the leading mobile anti-virus software, much like the situation when it was first discovered. Our investigation has revealed that this new variant of GinMaster has been injected into over 100 legitimate apps, which are then distributed on alternative Android markets.
TrustGo has named this new variation GinMaster.d.Trojan.Android.
GinMaster was first found by researchers from North Carolina State University on 8/17/2011. It is the first malware to utilize a rooting exploit that targets Android 2.3.3 (Gingerbread) devices, allowing escalation of privileges on the system. Once this exploit has been exercised successfully, GinMaster may install additional applications to the device without the user’s consent.
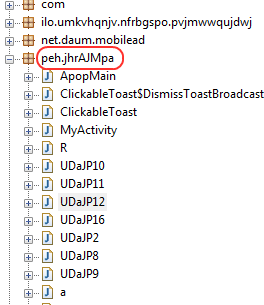
The most impressive feature of the original GinMaster is the extreme length it goes to in order to evade being detected by anti-virus software. For example, it obfuscates the class name for each infected object (see Figure 1). It is impossible to catch GinMaster by detecting the full class name.
Figure 1: Obfuscated class name
GinMaster also changes the URL address of its Command and Control (C&C) server to avoid detection. We have seen at least 3 C&C servers used by this malware:
http://client.mustmobile.com
http://client.139vps.com
http://client.go360days.com
The new variant of GinMaster we’ve discovered takes the above a step further; it actually encrypts these URLs!
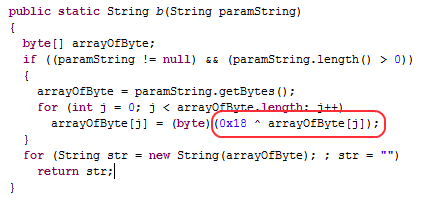
Figure 2 shows the encrypted string. It will be decrypted at runtime with the simple password 0×18 in Figure 3. We can see that the decrypted string is the C&C server’s URL address:
http://client.go360days.com/report/open_table.do
Figure 2: Encrypted string
Figure 3: Decrypt method
In the world of traditional PC viruses, polymorphic malware attempts to evade detection by encrypting itself differently, and rewriting the decrypting module accordingly. The newest variant of GinMaster now uses encryption as well, but the decrypting module is still static. It’s not a far stretch to suggest that GinMaster or another new malware could use a different cipher code for each decrypting module. With a dynamic cipher code, these pieces of software would effectively become the first known examples of polymorphic mobile malware.
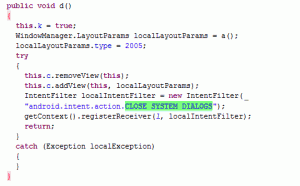
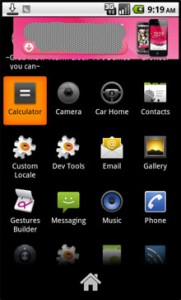
Besides the added encryption, the new GinMaster variant also extends its ability to control the user’s screen. It adds “View” by WindowManagerServices and sets the window type to “Toast”. The toast window can show on top of other applications even when the user has already quit the malware (See Figure 5).
Upon clicking the toast window, GinMaster will download applications and prompt the user to install them.
Figure 4: Screen control
Figure 5: Toast Window