Blog
Trojan!Extension.A – Complex Malware Escapes AV DetectionTrojan!Extension.A – Complex Malware Escapes AV Detection
By TrustGo Security Labs On February 4, 2013 In Categories
Recently, a new Trojan has been discovered that is designed to thwart detection by most AV apps. The TrustGo cloud service has been updated to identify and eradicate this new threat.
Trojan!Extension.A is based on the AspectJ framework (http://eclipse.org/aspectj/) and is injected into legitimate apps in alternative China markets. The infected code is highly obfuscated, thus making it extremely difficult to detect.
The Trojan is designed to download malicious code at runtime. Two files will be downloaded: release.xml and Extension-v1.6.apk. The first, release.XML, is needed by the AspectJ framework. Extension-v1.6.apk is an encrypted malicious Android package file that communicates with remote server and performs dangerous behaviors.
Extension-v1.6.apk is encrypted using DES algorithm. At launch, the Trojan will decrypt it, load it and execute its malicious code.
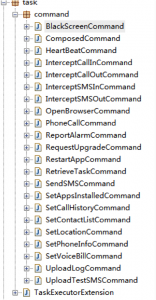
The following shows decrypted code from Extension-v1.6.apk.
According to remote server’s command, the Trojan is capable of:
- 1. Intercepting incoming and outgoing calls.
- 2. Opening a browser and visiting a specific website.
- 3. Execute clicks on advertisements.
- 4. Make phone calls.
- 5. Upgrade the malicious code itself.
- 6. Send SMS (recipient and message content are defined by remote server)
- 7. Collect privacy information on your phone, including call history, contacts, GPS location and device ID.
Recently, a new Trojan has been discovered that is designed to thwart detection by most AV apps. The TrustGo cloud service has been updated to identify and eradicate this new threat.
Trojan!Extension.A is based on the AspectJ framework (http://eclipse.org/aspectj/) and is injected into legitimate apps in alternative China markets. The infected code is highly obfuscated, thus making it extremely difficult to detect.
The Trojan is designed to download malicious code at runtime. Two files will be downloaded: release.xml and Extension-v1.6.apk. The first, release.XML, is needed by the AspectJ framework. Extension-v1.6.apk is an encrypted malicious Android package file that communicates with remote server and performs dangerous behaviors.
Extension-v1.6.apk is encrypted using DES algorithm. At launch, the Trojan will decrypt it, load it and execute its malicious code.
The following shows decrypted code from Extension-v1.6.apk.
According to remote server’s command, the Trojan is capable of:
- 1. Intercepting incoming and outgoing calls.
- 2. Opening a browser and visiting a specific website.
- 3. Execute clicks on advertisements.
- 4. Make phone calls.
- 5. Upgrade the malicious code itself.
- 6. Send SMS (recipient and message content are defined by remote server)
- 7. Collect privacy information on your phone, including call history, contacts, GPS location and device ID.